How it’s Happening and Five Steps to Take to Protect Your Network
When most people think of cutting edge cryptomining, they don’t think of using PLCs (Programmable Logic Controllers). Apparently criminal hackers and cryptominers think differently though! According to recent reports by Dragos, a major cybersecurity software company, criminal hackers have been gaining access to PLCs via password cracking tools laced with malware. The malware of choice is called Sality, which is a peer-to-peer botnet that performs tasks such as password cracking and cryptocurrency mining.
How’s It Happening?
First, we need to better understand how these bad actors are gaining access to some of manufacturing’s holy grail. They aren’t using sophisticated hacking techniques to bypass your team and your tool’s defenses. They are being invited in.
Imagine a scenario where one of your senior engineers unexpectedly passes away. Unfortunately for your company, this engineer wasn’t the best at documentation and preferred to store passwords in a notebook (wrong on so many levels) and no one can find it. Additionally, for the past 10 years or so, no one else has really accessed the PLC environment other than this engineer, if at all. So, your new engineer comes along and is desperate to get access to the PLCs as there are significant vulnerabilities that need to be patched.
So desperate, that they go looking for a password cracking tool.
***Stop here – If anyone on your team is seeking a password cracking tool from an untrusted, unverified site and then downloading it and using in your most sensitive environment…….your management team should be losing sleep at night (more on how to mitigate later).
Examples of these types of tools below – readily available for download on several websites, twitter, github, etc.
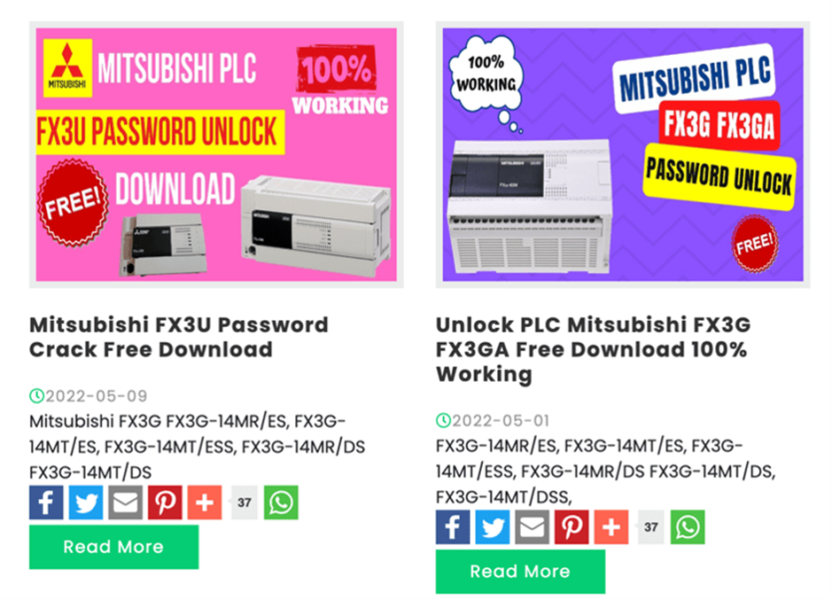
Once downloaded and introduced into your environment, the tool does do what it says, kind of. It doesn’t run your hashed or encrypted passwords through a password cracking rig with billions of word lists and misspellings like Rebyc Security would for our clients. Instead, it simply exposes vulnerabilities in PLCs that revealed the password. Your new engineer is happy – the password was retrieved, but…
Unfortunately, it also installed the Sality malware in your environment. And this is where PLC hacking goes current day. In years past, gaining malicious access to a PLC environment was typically used to conduct one of these:
- SURVEILLANCE
- Spend some time in your environment, see if they can elevate privileges or gain access to sensitive information or key staff.
- DATA THEFT
- Siphon off key information about your company: financials, HR, or intellectual assets such as schematics, designs, and product strategy.
- SABOTAGE
- Typically conducted on behalf of an unscrupulous competitor or a malicious attacker hell bent on creating mischief within your production environment.
For these attacks though, instead of the usual attack goals above, one of the current key initiatives is to steal cryptocurrency using your environment. Below is how Dragos described the attack:
“Sality employs process injection and file infection to maintain persistence on the host. It abuses Window’s autorun functionality to spread copies of itself over Universal Serial Bus (USB), network shares, and external storage drives. This specific sample of Sality also drops clipboard hijacking malware that, every half second, checks the clipboard for a cryptocurrency address format. If seen, the hijacker replaces the address with one owned by the threat actor. This in-real-time hijacking is an effective way to steal cryptocurrency from users wanting to transfer funds and increases our confidence that the adversary is financially motivated.”
Source: Dragos Blog – “The Trojan Horse Malware Password Cracking Ecosystem Targeting Industrial Operators”
Vendor and Asset (Includes PLCs, Project Files and HMIs)
For reference, Dragos tested a specific PLC using one of the password cracking tools they found available. However, they also noted that they found password cracking solutions for several PLC manufacturers as noted in the table below:
| Automation Direct DirectLogic 06 | Siemens LOGO! 0AB6 | Mitsubishi Electric FX Series (3U and 3G) | Weintek |
| Omron CP1H | ABB Codesys | Mitsubishi Electric Q02 Series | Allen Bradley MicroLogix 1000 |
| Omron C200HX | Delta Automation DVP, ES, EX, SS2, EC Series | Mitsubishi Electric GT 1020 Series | Panasonic NAIS F P0 |
| Omron C200H | Fuji Electric POD UG | Mitsubishi Electric GOT F930 | Fatek FBe and FBs Series |
| Omron CPM2* | Fuji Electric Hakko | Mitsubishi Electric GOT F940 | IDEC Corporation HG2S-FF |
| Omron CPM1A | Fuji Electric Hakko | Mitsubishi Electric GOT 1055 | LG K80S |
| Omron CQM1H | Pro-Face GP Pro-Face | Vigor VB | LG K120S |
| Siemens S7-200 | Pro-Face GP | Vigor VH |
How to Protect Against It
Obviously, not having employees download malicious software and running it in your environment is number one, but how does your management team ensure that kind of protection without constant oversite? The best way to protect your PLC’s is to protect the network providing access to them. Below are five steps you can take to protect your network and your PLCs:
- EMAIL FILTERING
- Regularly testing spam filtering rules to ensure they are appropriately blocking the latest types and styles of phishing attacks.
- WEB FILTERING
- Blocking access to uncategorized sites and sites that are less than 30 days old will greatly decrease the chances of an employee accessing and installing malicious software.
- PRINCIPLE OF LEAST PRIVILEGE
- Ensuring that users only have the permissions and access required to do their day-to-day jobs. Many end users do not require the permissions required to install software and should not be assigned such levels of access.
- APPLICATION WHITELISTING
- Utilizing an application to whitelist “allowed” software and services to run within your environment will help ensure unauthorized, malicious programs can’t be run.
- EMAIL USER AWARENESS TRAINING
- Employees should be training on the importance of cybersecurity and understand the current threats and attacks in the industry as well as best practices to keep themselves and the organization safe.
Bringing in an offensive security consulting expert like Rebyc Security can help find where you are most vulnerable to attack and provide remediation strategies. If your organization wants to have a consultative discussion about best steps to take to secure your network, let’s talk. Rebyc Security can provide cybersecurity guidance and testing to help secure your most valued assets. Reach out to info@rebycsecurity.com or you can contact us via our website at https://www.rebycsecurity.com/



