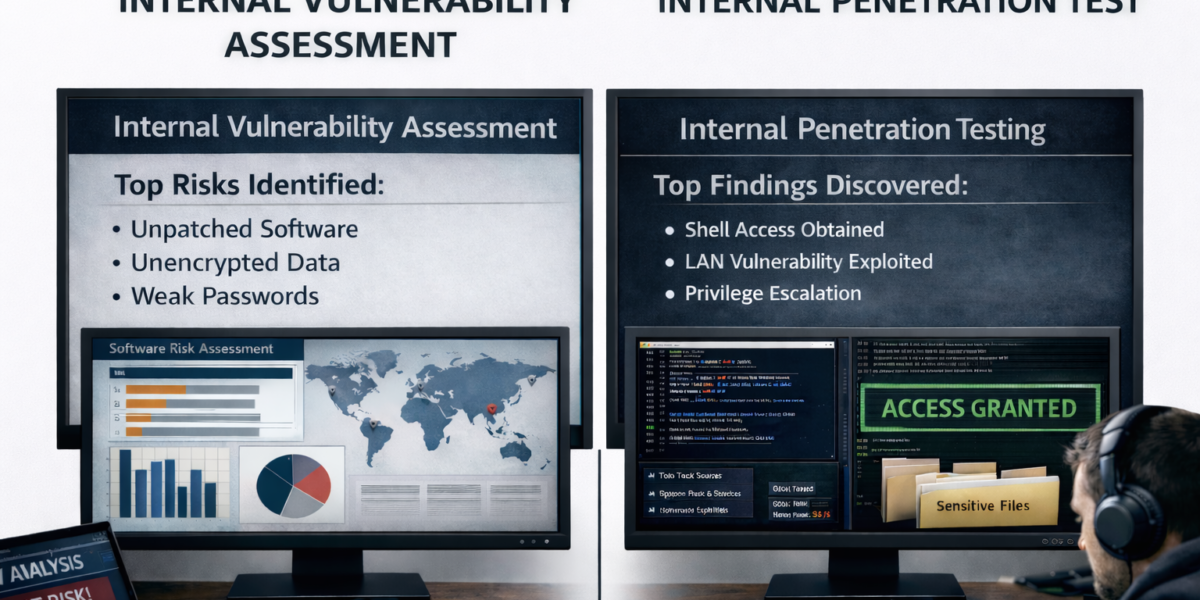
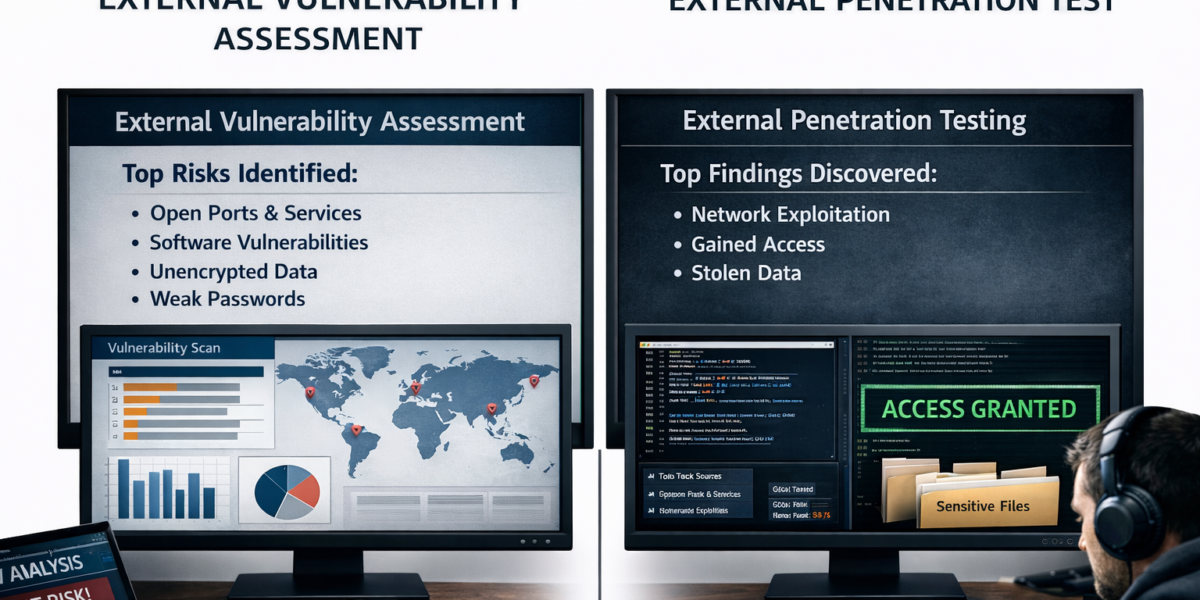
You’ve invested heavily in ransomware defenses. Firewalls, endpoint protection, backups, email security, and an incident response plan are all in place. On paper, your organization looks well protected.
And yet, attackers are still getting in.
The uncomfortable truth is that many successful breaches today don’t begin with ransomware, zero-day exploits, or sophisticated malware. They begin quietly—often months or even years earlier—with infostealers: malicious programs designed to harvest credentials, authentication tokens, browser cookies, and sensitive data without alerting the victim.
Infostealers represent a silent epidemic. They don’t announce themselves. They don’t disrupt operations. And they often slip past security controls entirely—until the day stolen credentials are used to authenticate legitimately and walk straight through the front door.

Infostealers Aren’t a Malware Problem — They’re an Identity Crisis
Modern security architectures are built around identity. We authenticate users, validate devices, and enforce access controls to protect systems and data. Infostealers undermine this model by stealing trusted identities at scale.
Once an attacker possesses valid credentials or active session tokens, they no longer need to exploit vulnerabilities. They authenticate like legitimate users. Firewalls don’t stop them. Endpoint tools don’t flag them. And security teams often miss the initial compromise because nothing appears overtly malicious.
In practice, this is why infostealers have become one of the most effective initial access vectors in modern attacks—and why identity-centric testing has become increasingly important. In assumed breach exercises focused on Microsoft Entra ID environments, for example, testing often begins with valid credentials rather than malware execution, reflecting how real attackers now operate.

What Infostealers Actually Do in 2026
Infostealers are lightweight malware designed for data harvesting, not disruption. Once installed—typically via phishing emails, malicious downloads, cracked software, or compromised websites—they immediately begin collecting high-value information, including:
- Saved browser credentials and autofill data
- Session cookies and authentication tokens
- VPN, email, and cloud service credentials
- Password manager data
- Cryptocurrency wallets and financial information
The stolen data is exfiltrated quietly, often over encrypted HTTPS connections or posted directly into attacker-controlled Telegram or Discord channels. Because infostealers operate quickly and don’t encrypt files or cause obvious damage, they frequently evade endpoint detection and response (EDR) tools.
In many cases, the victim never knows they were infected.
This is why credential exposure research—such as reviewing infostealer logs and underground marketplaces during reconnaissance—has become a practical way to understand real-world risk. Efforts like Rebyc Recon focus on identifying whether employee credentials already exist in infostealer datasets, providing early insight into exposure long before an intrusion is detected internally.

Why Traditional Security Controls Miss Infostealers
Infostealers exploit the gap between prevention and visibility.
They don’t behave like ransomware, so they don’t trigger alarms. They don’t require privilege escalation, so they blend in with normal user activity. And once credentials are stolen, the malware itself often becomes irrelevant—the damage is already done.
Common assumptions that break down in these scenarios include:
- “We use MFA, so we’re protected.”
MFA significantly raises the bar, but stolen session tokens can bypass it entirely. Token replay and adversary-in-the-middle techniques are frequently demonstrated during assumed breach testing against cloud identity platforms. - “We rotate passwords regularly.”
Rotation doesn’t help if endpoints are reinfected or if valid tokens persist beyond password changes. - “Our SOC monitors for suspicious activity.”
Valid logins from compromised accounts often appear normal, especially when they originate from familiar devices or geographies.
This is not a failure of security tooling. It’s a failure to test identity abuse scenarios realistically.

The Infostealer-to-Ransomware Kill Chain
Infostealers rarely cause immediate damage. Instead, they act as the first stage in a longer attack lifecycle:
- An employee unknowingly installs an infostealer on a personal or corporate device
- Credentials and session tokens are harvested
- Stolen data is sold or shared on underground markets
- Months—or years—later, attackers use valid credentials to access VPNs, email, or cloud platforms
- Lateral movement occurs under a legitimate identity
- Ransomware deployment or data exfiltration follows
In many real-world cases, attackers rely on credentials harvested long before the breach—sometimes years earlier—that were never invalidated.
Ransomware is not the beginning of the attack.
It is the final act.
By combining credential exposure intelligence (such as Rebyc Recon findings) with assumed breach testing that starts from valid identities, organizations can better understand how far an attacker could progress before being detected.

The BYOD and Personal Device Blind Spot
Infostealers are no longer confined to corporate endpoints. A significant portion of harvested credentials now originate from personal devices employees use to access work resources.
Consider a common scenario: an employee checks work email from a home laptop. A family member downloads a malicious game mod. An infostealer installs silently. Credentials are harvested—and months later, those credentials are used to access corporate systems.
This isn’t hypothetical. It’s happening every day.
When organizations assess credential exposure through reconnaissance efforts and then test identity-based access paths during assumed breach exercises, this personal-device risk often becomes visible for the first time.

How Organizations Should Respond
Defending against infostealers requires shifting focus from perimeter security to identity resilience.
Foundational Controls
- Phishing-resistant MFA for critical systems
- Strong password hygiene and password manager adoption
- Visibility into all devices accessing corporate resources
Advanced Controls
- Conditional access policies based on device posture
- Token lifetime management and rapid revocation strategies
- Monitoring for abnormal—but valid—login behavior
Proactive Controls
- Ongoing credential exposure monitoring
- Assumed breach testing using valid credentials and tokens
- Detection and response testing for compromised identities
When these controls are evaluated together—credential exposure on the outside and identity abuse on the inside—organizations gain a much clearer picture of their real risk.

Questions Leaders Should Be Asking
- How quickly can we detect stolen credentials being used?
- Do we monitor for token-based access abuse?
- Can we identify risky access from unmanaged devices?
- Have we tested our ability to stop an attack that starts with valid credentials?
If these questions don’t have clear answers, infostealers remain a hidden vulnerability.


Test Your Defenses Before Ransomware Does
Attackers already assume credentials are compromised. Modern security strategies must do the same.
By pairing credential exposure reconnaissance with assumed breach testing focused on identity abuse, organizations can uncover blind spots long before ransomware appears. These exercises reveal whether monitoring detects compromised access, whether incident response teams act quickly, and whether small identity failures can cascade into major breaches.
Understanding how an attack unfolds before ransomware is deployed is no longer optional—it’s foundational to defending modern environments.
Rebyc Security offers two services to address many of the challenges outlined above.
- Rebyc Recon shows what exposure already exists
- Microsoft Entra ID Assumed Breach Testing (Details of service on our home page) shows what that exposure enables and answers these questions:
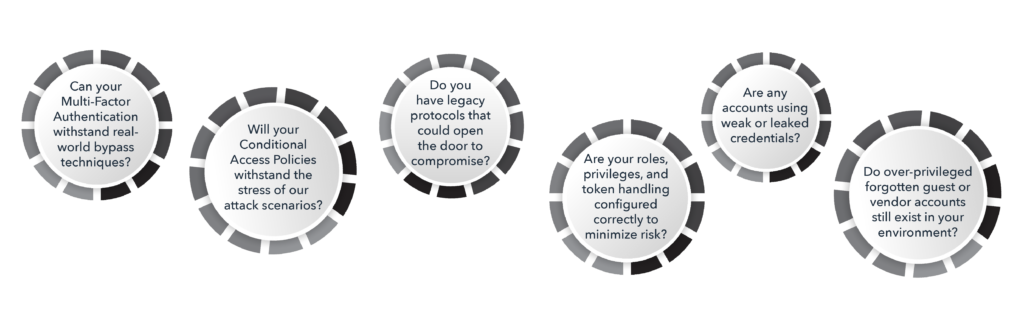
Together, they turn abstract identity risk into measurable, testable reality.