Over the past few years, we’ve traveled the country with Jack Henry and Associates putting on Cyber Risk Forums for hundreds of banks and credit unions. At each event, we always ask what’s keeping you up at night from a cybersecurity perspective. While we get a number of different answers at each event, PHISHING is always number one – Always. Quite frankly, we don’t expect that to change any time soon.
As we talked with our clients and prospective clients, we learned that many of them are utilizing KnowBe4 for their phishing assessments and phishing-related employee training. (Full disclosure, Rebyc Security is an authorized reseller of KnowBe4.) It is an excellent tool to automate phishing assessments and to raise general awareness around the dangers associated with phishing. On average, our clients that utilized KnowBe4 saw a 27% decrease (30% to 3%) in employee credential theft within the first 12 months! High-Fives and pats on the back all around (before social distancing was in effect!) That was easy, right? WRONG!
You see, it just wasn’t adding up for us. When we did our custom phishing engagements, we were still getting results in the 20% to 30% range. Even for our clients who told us they had reduced their click rates by using training and awareness programs. And, keep in mind, even a phishing test with a 3% click rate, is still ENOUGH – we only need ONE.
So, if so many companies are doing such a good job (per their phishing solution reporting at least), then why are we still seeing all these headlines:
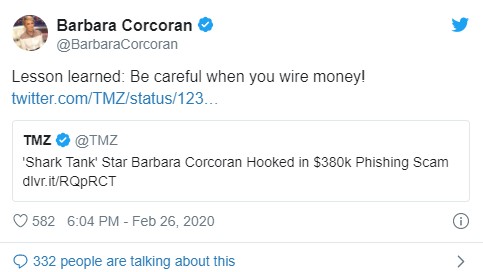
- Barbara Corcoran, real estate mogul and Shark Tank alum, lost close to $400K in an email wire fraud attack. (Update: she was able to recover her funds, but this is certainly the exception, not the norm.)
- Brian Krebs recently wrote that the Target breach started with a phishing attack.
- In February, the Puerto Rico Government announced that it had been duped out of $2.6M in an email phishing scam.
We could keep posting examples like the ones above, or employees clicking on links, or Coronavirus scams, or ransomware attacks. It’s endless.
So, to find out why the discrepancies between the results we were hearing about and the results we were getting in our testing, we hit the bricks. We wanted to talk to the front lines and figure out why all the reported success wasn’t reducing the headlines.
Let’s Talk to the Users!
One of the benefits to the Cyber Risk Forums as well attending the Jack Henry Annual Conference and the Symitar Educational Conference is that we get to hear perspective from thousands of financial industry attendees every year! What we began hearing is that after 18 to 24 months of phishing their employees, some people felt that the employees were beginning to catch on. There are only so many templates, domain names and premises for enticing an employee to click a link that can be packaged into an automated solution like KnowBe4. Eventually, employees began to pick up on the domain names, the formatting, the premise of the campaigns etc. We aren’t going to point any fingers, but we’ve heard of some folks keeping and sharing lists of the domains and emails and even creating rules in Outlook to make sure they don’t fail the tests! While we applaud the creativity and ingenuity of some users, it isn’t helping the organization stay secure.
6 Questions to Ask
To help organizations answer the question “Are You REALLY Phishing Your Employees?” we’ve put together 6 key points you should be considering when conducting phishing assessments:
- Is open-source intelligence gathering being utilized to create realistic campaigns?
- Company Website, LinkedIN profiles, employee social media accounts, web forums etc.
- Have you spoofed someone from within your organization using a misspelled domain or different top-level domain?
- .net .co .us .info .mobi .live
- Do you spoof vendors / suppliers that regularly contact employees at your organization?
- Do you purchase misspelled domains for these vendor-based campaigns?
- Are campaigns based on timely, realistic scenarios?
- WebEx and Zoom invites/installs
- Covid-19 Updates
- Economic relief scams etc.
- Do you follow up to your phishing emails with:
- Text messages?
- Telephone calls?
- Another phish?
- Have you simulated a compromised email account attack against high profile targets within your organization?
If you aren’t challenging your employees with some of the above scenarios, rest assured someone else will. Because of risk associated with phishing and client conversations, several of our clients engaged Rebyc Security to conduct realistic, fully customized phishing assessments against their organizations.
The results? Not so great! We saw the average failed phishing campaign increase approximately 32% compared against KnowBe4 results. Yes, some of our emails were in fact caught by the spam filter, but many were not. Sometimes our websites were blocked by a web filter, sometimes they weren’t. We’d be remiss if we didn’t take this opportunity to point out that phishing assessments are specifically designed to test the human response element, not to see if your spam and web filters are working (yes you should be testing those systems as well!). These results clearly illustrated that well-formed phishing campaigns that build initial trust can still be very successful today.
4 Key Tips to Consider
Here are some tips that Rebyc Security has picked up over the years to help your organization and employees stay safe and remain vigilant against phishing attacks:
- Vary Your Testing
- Make sure that systems like KnowBe4 are supplemented with real-world, custom phishing attacks against your organization and/or high-risk employees.
- Test Spam and Web Filtering
- Ensure spam filters are tuned to block latest threats.
- Consider blocking access to uncategorized websites and/or websites less than 30 days old.
- User Awareness Training
- Continue to create up-to-date, relevant security related content.
- Make sure employees understand the risks associated with phishing and the impact of failing.
- Multi-Factor Authentication
- For any Internet-facing resources owned or utilized by the organization, MFA should be enabled.
If you have any questions regarding phishing, want to discuss our custom phishing programs any other information security related needs, please feel free to contact us through our form on the bottom of the page.



