Your Bank or Credit Union is Getting Phished – Rebyc Can Help
Rebyc Security partnered with Jack Henry & Associates Profitstars Gladiator team to deliver six Risk Forum events for financial institutions. At each event, the attendees were asked “what keeps you up at night from a cyber security perspective?”.
Across all six events, the overwhelming response was the same — phishing scams.
Today’s mitigation strategies, phishing awareness, and staff training make it continually more difficult for attackers to penetrate banks and credit unions. Yet with all the advancements in security, phishing is still one of the most successful and widely used forms of modern hacking. The scams continue to get more sophisticated, and simply stated, they work.
This blog post breaks down phishing examples IT departments are most concerned about at their bank or credit union.
1. Spear Phishing
Spear phishing is a targeted attack towards a specific individual, group or business with malicious intent. Typically, attackers are looking to get credentials and or gain access to sensitive information.
- This attack targets senior leaders and entry level employees just the same. While an entry level employee might not have the authority or administrative access of a more senior employee, gaining access to their credentials can allow an attacker to listen, pivot, use information in their emails, etc. to target other more attractive accounts.
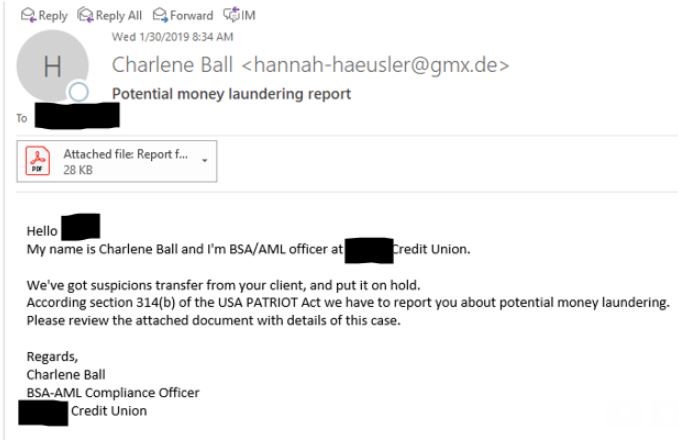
- Earlier this year, BSA officers within several credit unions received emails made to look like they were coming from BSA officers at other credit unions. The sender of the message claimed to have received a suspicious (or more specifically – “suspicions”) transfer and needed to report the receiver of the email for money laundering reasons. They were then asked to open the attached PDF for details. While the PDF itself was clean in most cases, it contained a link to a malicious site.
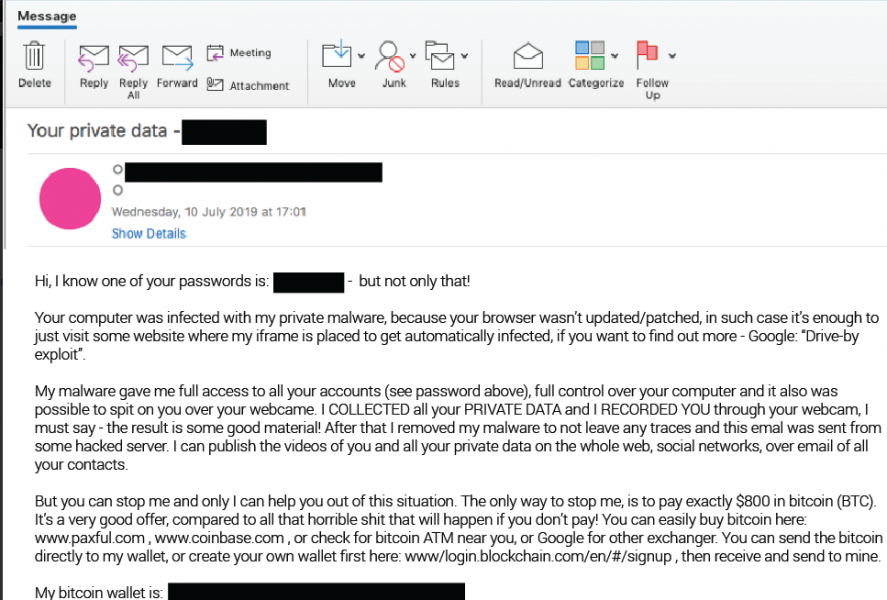
- Taking Spear Phishing even a step further, some attackers attempt to go after their targets using very sensitive information. For instance, Cofense Labs recently released a list of 200M+ emails and domains that they believe are part of a sextortion campaign. While some bad adversaries could just do a blanket campaign to see how many victims they could get, the data could also be uses to spear phish intended targets. The attackers could shame the victims into providing info, data, or access in order to keep from getting exposed. Below is an example of such a phish:
2. Romance Fraud
While this type of fraud dates back many years, the newest version of romance fraud uses mobile app dating sites, such as, Tinder, Bumble or Match.com to phish victims.
- The bad actors use fake identities to build a relationship online with their victims first, and then start asking for help. Many times, they pressure their targets to leave the site they met on and begin communicating through personal email or messaging.
- They tend to claim to be in the military or traveling overseas and need their victim to wire money to buy a flight, send a gift card to help with medical expenses or claim some other hardship while playing on the emotions of their new connection.
- According to the 2018 FBI Internet Crime Report, there were over 18,000 cases of romance fraud resulting in over $362 million in losses. Those numbers represent a 20% increase in cases and more than a 70% increase in losses as compared to the 2017 report.
3. Business Email Compromise
There are many types of Business Email Compromise (BEC) phishing examples, but essentially, it begins with a fraudster spoofing an email from an executive at a company, attempting to get an authorized employee to generate a wire. Ironically, Romance Fraud can also lead to BEC as unsuspecting banking clients can be asked to create accounts for the attackers. Then, those same fraudsters can use those accounts to funnel money through from other attacks.
In many cases, with BEC, the fraudster has had access to the compromised email account for some amount of time. They’ve figured out how the executive interacts with staff, how they ask for tasks to get completed, and what is the tone they use in their communication. In one communication, an attacker, who was asking for a wire transfer, asked the victim how her son was doing after his knee surgery. That’s the type of relationships they build in order to pull off their con.
According to a recent Dark Reading article, BEC attacks were up 67% in 2018, and 73% of those attacked reporting experiencing losses. The only fraud that was more successful than Romance Fraud? Business Email Compromise resulted in almost $1.3 billion in victim losses in 2018.
So How Can Banks and Credit Unions Protect Themselves and Their Clients from Phishing Attacks?
Your organization and your people are going to get phished. It doesn’t matter if you are 50 employees or 10,000, the likelihood that hackers are going to find success with at least 1 employee, is high. Despite all the best training, monitoring, and investments in tools and technology, it’s still likely you’ll have an employee take the bait.
The best thing financial institutions can do to avoid being phished is to be aware and create a plan to limit the damage. Here are eight strategies to help you reduce the risk.
8 Strategies to Help Reduce the Risks Associated with Phishing
- Test and tune web and spam filters to protect users against the latest phishing campaigns
- Consider using a whitelist only web browsing policy, or block access to uncategorized and web sites less than 30 days old
- Properly configure your Bank’s Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM) and DMARC records
- Setup an email address (i.e. spam@banking.com) for employees to direct potential spam emails to the appropriate personnel for verification
- Apply multi-factor authentication for any externally facing banking resources
- Utilize the principle of least privilege when assigning user access rights
- Remove local administrator rights from end-users
- Train users on the importance of strong, secure password creation
The strategies above constitute a good basis for addressing your institution’s phishing exposure. While there are some good tools for training and awareness, at Rebyc Security, we take it a step further and truly customize a phishing engagement that mimics a real wold attack.
Have questions or just want to learn a bit more? Let’s talk about how Rebyc’s can help advance your awareness and reduce your risk.