6 Questions to Find Out If You Are REALLY Phishing Your Employees
Over the past few years, we’ve traveled the country with Jack Henry and Associates putting on Cyber Risk Forums for hundreds of banks and credit unions. At each event, we always ask what is keeping you up at night from a cybersecurity perspective. While we get several different answers at each event, PHISHING is always number one – Always. Quite frankly, we do not expect that to change any time soon.
There are so many fresh opportunities (for lack of a better term) to target your institutions these days. As an institution, you are at your most vulnerable point right now. Your employees are working from home using potentially unvetted personal devices. They are getting inundated with coronavirus scams, malware laced email attachments and fake websites spoofed to look like Covid-19 heat maps showing where it is most prevalent.
Search terms like “Coronavirus Map used to spread Malware” or “Coronavirus Scams” or “Nation State Government Hackers Craft Covid-19 Phishing Emails to Distribute Malware.” We could cite several more recent examples of employees clicking on links, or Coronavirus scams, or ransomware attacks. It is endless.
The bad actors, they are busy right now. They prosper in times of crisis. They love using fear to motivate even the most well-trained employees to open an attachment or click a link that know they should not. And all it takes is ONE.
A good example of only needing ONE
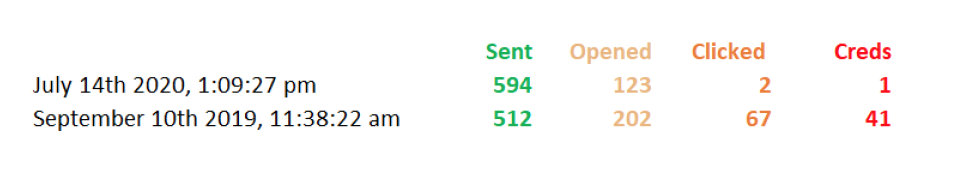
In the case below, we conducted two phishing tests with a client of ours, 10 months apart. This was a semi-custom attack using a spoofed leadership email asking for employees to click on a link and update their credentials. As the results show, they had significant improvement across the board, especially in the two key areas, clicked and credentials.
A key note here about these results…..They are not typical. In a lot of cases, we see improvement, sure, but this was significant improvement. This client was extremely concerned with those September outcomes. They had Senior Management buy in to make changes and implement new policies and procedures as needed. In the time between the tests, they spent time answering the questions we pose further down and had Rebyc conduct in person lunch and learn training sessions with all staff.
By all accounts, they did a lot of things right and their results revealed those efforts were successful. Major improvement. But see the ONE in red under the “Creds” header? It mattered.