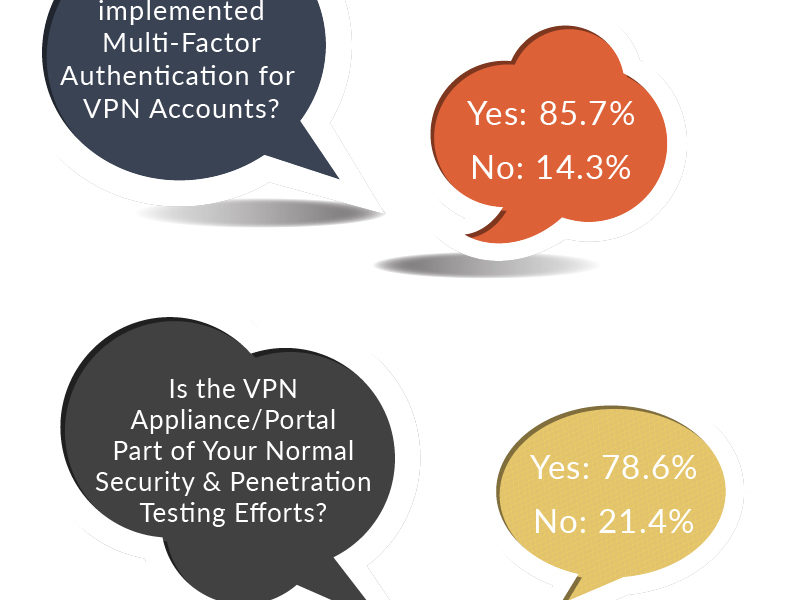
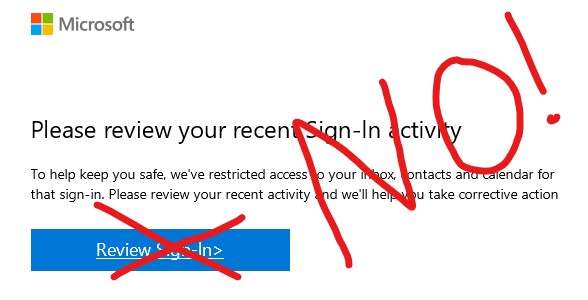
Focusing on Virtual Private Networks and Phishing Schemes Can Help Solve These Problems Your jobs as chief information officers (CISOs) were already tough. Then the pandemic hit. And your jobs got much mor...
NEWS RELEASE DATELINE: Charlotte, North Carolina FOR IMMEDIATE RELEASE: June 15, 2020 — Rebyc Security today introduces cyber security penetration testing services to help proactively address new and growing ...
Take some Covid-19 restrictions, mix in some teenage daughters, bad lighting, wind, sun in our eyes, horrible background, terrible acting, 8 weeks past getting a haircut and the script sticking out of my pocket…..a...
Over the past few years, we’ve traveled the country with Jack Henry and Associates putting on Cyber Risk Forums for hundreds of banks and credit unions. At each event, we always ask what’s keeping you up at night ...
If we’re thinking like criminal hackers, guess what we’re putting together – A government stimulus check #phishing attack. As of this writing, a $2 Trillion stimulus package has been passed with checks...
Let’s get real for a minute – like Chris Roberts real. If you don’t know or know of Chris and you work in cybersecurity or information security, he is a good follow. His posts are always on point, relevant, a...
Unfortunately, due to the Coronvirus, we have to postpone all of the Spring Cybersecurity Forum events. Please stay tuned as we are planning to reschedule. Be safe! Rebyc Security is excited to announce our next r...
In the sporting world, they call it a road trip anytime a team from one coast takes an extended trip to the other coast. Rebyc Security recently went on a West Coast Road Trip, attending and exhibiting at both the ...
Your Bank or Credit Union is Getting Phished – Rebyc Can Help Rebyc Security partnered with Jack Henry & Associates Profitstars Gladiator team to deliver six Risk Forum events for financial institutions. At eac...
In the link below, Hiscox Insurance produced a short video detailing the business impact of a cyber breach. It’s well done and in only 3 minutes, gives quite a visual representation of what a behind the scenes hack migh...